
Mentioned in this post…
- 4 Easy Steps to Take to Minimize Opening a Risky Email
- 5 Immediate Next Steps to Take if You Are Victim to a Spoofing Attack
- 3 Ideal Security Practices to Incorporate into your Business
- How to Tell Your Customer or Clients
- LastPass [Password Security]
- Gmail
- Google Chrome
- Contactually [Customer Relationship Management (CRM) Service]
Up until March 7th, 2018, I had been lucky enough to avoid any impersonators or scammers directly related to my own email addresses.
Fast forward to March 7th…
…and I joined the club that so many other individuals and business owners have been unintentionally inducted into. I discovered that someone or something was pretending to be me sending out emails to my contacts.
Yikes! I was victim to what is called a spoofing attack. This is when “an attacker or malicious program successfully acts on another person’s (or program’s) behalf by impersonating data” (according to CheckMarx). The attacker pretends to be someone else (or another computer, device, etc.) in order to trick other computers, devices or people into performing legitimate actions or giving up sensitive data.”
My first response? SHUT THE FRONT DOOR!
Let’s just say I wanted to say more than that…but I kept it classy when talking with my team. The bummer was that it was an old email address that I’m not longer even using. I hadn’t deleted it just yet, and then this happened.
I value my clients so much that I couldn’t just ignore the situation and let it blow over. I felt it was right and necessary to let them know that the old email address was no longer in use and that they should NOT click on any links in the email that was sent out to them.
In going through this frustrating process, my team and I have learned some very valuable lessons that we felt would be beneficial for other business owners and individuals to know so that their risks of compromise can be minimized moving forward.
I’m going to let Athena, my Operations Director, share the top lessons we learned from this exercise, and what we want you to know, so that hopefully you don’t have to go through anything like this in the future.
Or if this does happen to you, you will be a few steps smarter to recover faster.
Hello, there! I’m Athena, Operations Director here at KathleenMetcalf.com.
We’ve gathered tips for identifying risks so that you can minimize how you’re impacted by spoofing attacks or phishing events and we’ve also included basic tips for what to do if you may become a victim. We’ve also shared what we did and how we chose to approach our customers about it.
While we may all hope that we don’t become victims of spoofing attacks or phishing events, the reality is that these events happen daily and are becoming more and more sophisticated. We need to remember to be more aware so that we can spot red flags.
4 EASY STEPS TO TAKE TO MINIMIZE OPENING A RISKY EMAIL
1. First things first, check the sent email address. Not just the name because anyone can write anything in as the name. Check that email address.
They’re getting so good at blending in. You’ll see company logos being used – same branding colors and fonts, even supposed unsubscribe links, but they are spoofing or phishing emails.
If the sender is claiming to be MailChimp, for example, their email address shouldn’t be honsec1@bombaybar.com. Or, if they’re claiming to be Microsoft, their email address won’t be latoya.stewart@elcomutual.com. Examples included below.
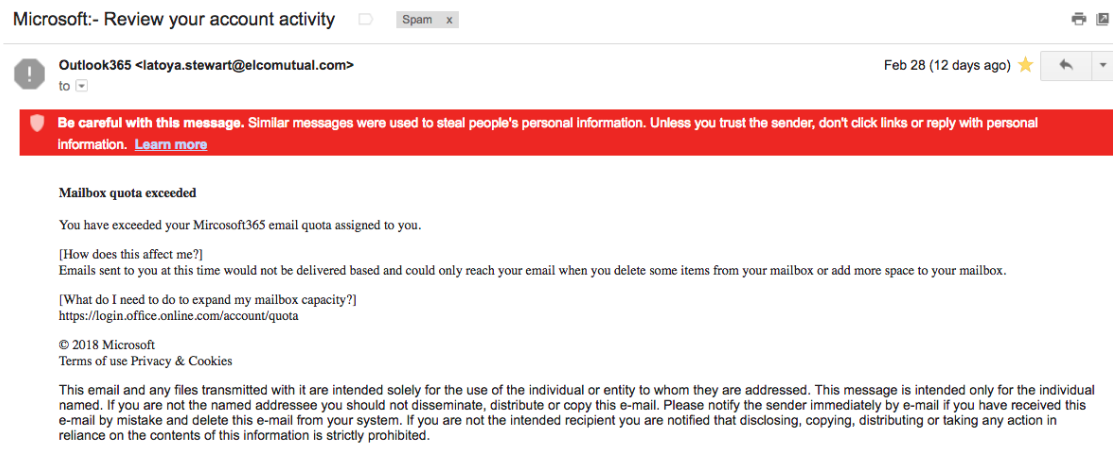
The tricky thing is that it isn’t glaringly obvious. There are small indicators that will tally up to indicate that you shouldn’t believe the email and that you shouldn’t follow the action they are asking from you. We have to pay attention to the nuances more and more.
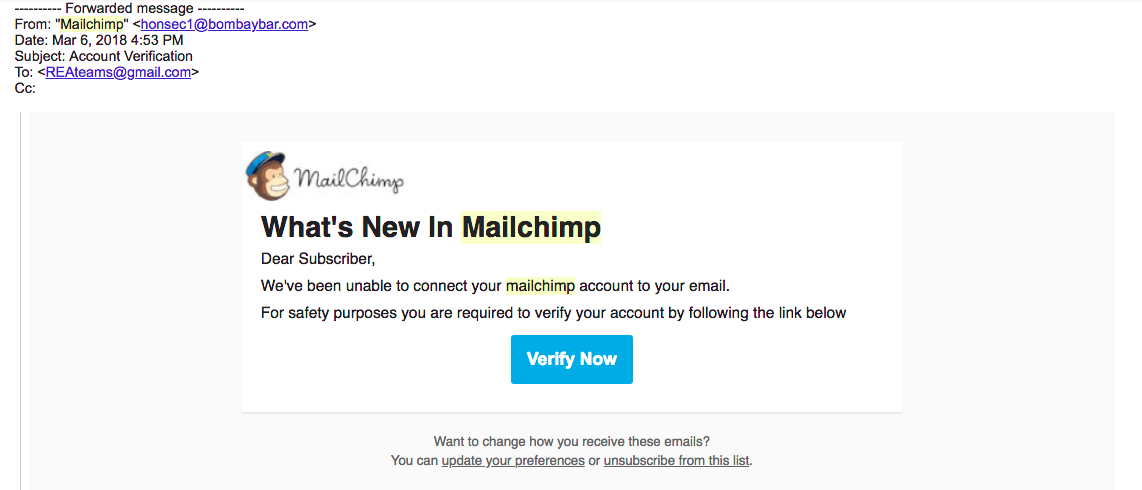
False MailChimp email:
Versus an actual MailChimp email:
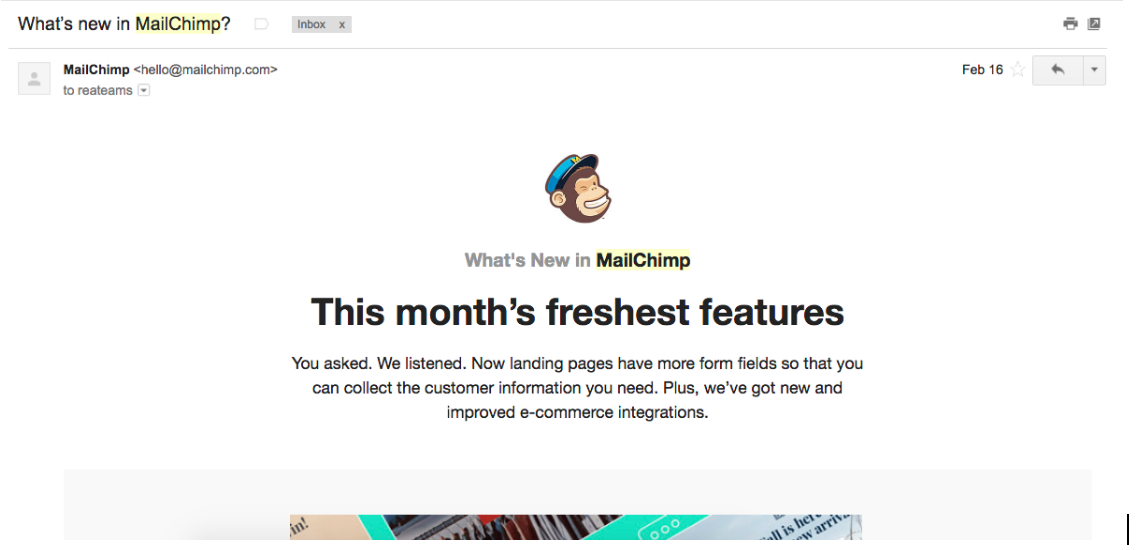
2. Be very wary of ANY email asking for sensitive information like account verification or confirmation when you have not initiated the steps to prompt this.
When someone fraudulently sends an email that appears to be coming from a reputable company in order to get the recipient to reveal personal information, like passwords or credit card numbers, this is called phishing.
What’s worse, they play on your existing concerns of security to frighten you into doing something you shouldn’t do.
“We’ve been unable to connect your MailChimp account to your email. For safety purposes you are required to verify your account by following the link below.”
“We’ve noticed unusual activities in your account and as a result, your Squarespace orders have been placed on hold.”
It’s better to always go to the source directly than to trust an email message. Call the support line or start an email chat directly with the provider. Don’t be eager to click on links, to share your passwords, or your credit card information easily.
You may have a team member that is trying to update your records or make changes to settings within your apps/programs/etc., but make sure you ask questions of your team members to confirm that it was indeed initiated. Try not to assume that it was someone on your team and then click on things you shouldn’t. Kathleen will do this with me and sometimes I have initiated something, but other times, it’s a hoax.
When you identify that the sender is NOT the person or company they are claiming to be, DO NOT follow the link and DO NOT enter your information. Your team member may be stunted in their progress, but your peace of mind, and the safety of the business, is so much more important.
3. Do you notice other odd or unusual signs? Is the subject line uncharacteristic of the sender? Does it seem spam-like?
Luckily, Gmail does a really great job of catching phishing and spoofing emails for their users and they alert their users to the fact that the email is suspicious. Outlook email, as we found in our research, isn’t as secure as Gmail.
So, if you’re not using Gmail, you’ll also want to pay attention to the things that seem off. We received emails from our contacts that said something along the lines of “I got an odd email from you that…”. They noticed that is was off and sent a separate email to follow up on whether it was a legitimate email or not. There is no harm in this double checking if an email from the sender is legitimate or not. Safety is important! Safety first, then teamwork.
The impersonator in our incident used the branding of Docusign to make the email seem more legitimate, but the subject line “Treat ASAP” was not what our customers are used to seeing from Kathleen. It was out of context for many.
If it seems off or odd or weird, it most likely is. It’s better to reach out to the sender to ask questions and confirm than to click on uncertain links in emails.
4. Use 2-step authentication where possible.
This adds another layer of protection to your account. It is harder for an impersonator to have access to the second step of verifying the account of login details. Lots of providers these days allow for 2 step authentication requires so see where you can protect yourself more with this option.

5 IMMEDIATE NEXT STEPS TO TAKE IF YOU ARE VICTIM TO A SPOOFING ATTACK
We turned to all of our different software providers in the hopes that they could investigate and find out more about how it all happened. We came to find out that they don’t do this – they don’t investigate. They rather emphasize security and good security practices to help reduce the chance of spoofing attacks from happening. With their guidance we learned to do the following:
- Immediately change passwords. As a general practice, change your passwords at least quarterly and don’t use the same password across multiple apps/software/etc.
- Initiate 2 step authentication for logins especially where your most valuable information is housed, if not everywhere. 2 step authentication requires you to do an additional verification step in order to sign in. Depending on the provider, this could be a security question, or to enter a code that is sent to your cell phone or using an app password.
- Make sure no forwarding emails were added to your account. Also check your contact information in that app/software to make sure it wasn’t changed to someone else. This is how the attackers keep you out of the loop so you don’t see you’re getting replies to emails you didn’t send. This didn’t happen to us, but it’s good to double check.
In Outlook, you can also create certain rules for your email. You can set up an automatic forward to other email addresses. Make sure to delete any rules that may have been added that you didn’t initiate.
- Add the settings that send alerts for suspicious sign-in activity and any other actions that you would want to know about (that are available with your provider).
- Enable the pop-up blocker for your browser. Chrome is the safest browser out there. Especially if you’re not on Chrome, be sure to enable your pop-up blocker so you can minimize your interaction with potential viruses.
Side note: Chrome is available for smartphones as well and it has some really awesome syncing capabilities with your desktop or laptop Chrome.
3 IDEAL SECURITY PRACTICES TO INCORPORATE INTO YOUR BUSINESS
Stay a few steps ahead of risks by incorporating these 3 practices.
- Delete old email accounts that aren’t in use. Because you aren’t in them frequently (or ever), they aren’t being watched and you aren’t seeing what is going in or out. We were holding onto our previous email address ‘just in case’. This exercise has shown us that we didn’t even need the email address any longer.
- If you change your domain, keep registering the old one so that no one else can have access to it in the future. People with bad intentions can come along and pretend to be you by using your old domain and taking advantage of your history.
- Change your passwords regularly. We use LastPass for our passwords. Kathleen and I can share access to the same logins and passwords to certain select accounts. There are free and paid versions. Check it out for yourselves. The days of passwords on post-it notes and Excel spreadsheets is not safe and outdated. Find a secure way to save all the different logins and passwords that you use in the business even if it isn’t LastPass.
HOW TO TELL YOUR CUSTOMERS OR CLIENTS
We weren’t sure who received this spoofing email or not, so we decided to contact everyone in our database. This way everyone could know not to rely on emails sent from the old email address that was no longer in use. We had intended to proactively email everyone in the database with an update about the email address no longer being used, but this incident beat us to it.
There was no record in any email in our sent folders so we were in the dark as to the extent of the reach of the attack. We value our contacts and relationships and so we reached out to ALL OF OUR CONTACTS.
Do you have a way to be able to email all of the contacts in your database at once?
We didn’t. We have daily limits on our CRM and Gmail does too (150-200 emails/day). We wanted the emails to come as directly from us as possible. With MailChimp, we were concerned the emails would end up in Spam folders and battle opt-in issues, so, although limiting, we used our CRM (Contactually). It took us several days to send an email to each contact. We wanted to protect our contacts so we told everyone.
We hope we’ve given you some insight into how you can try to avoid these kinds of issues from arising from spoofing or phishing events moving forward.
Remember:
- it’s better to be safe than sorry
- pay attention to the red flags
- ask questions to confirm before following links
- stay aware out there!
Our hope is that you’ve learned something new and valuable from our experience. We love hearing from our readers and clients so that we can share resources and experiences that would be helpful to you.
Share your requests and suggestions with us by email or by using our contact form here.
Thank you for your loyalty and communication with us! We value each and every relationship. Let’s stay in touch!
– Kathleen, Athena & Team

